 |
 |
 |
| Bandwidth Management with Identity Reporting |
|
|
 |
 |
 |
|
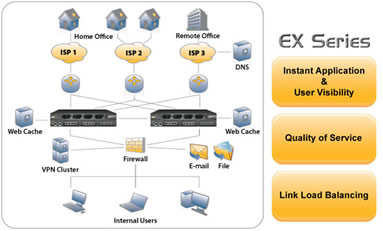
A10 Networks' EX Series is the industry's only bandwidth management appliance with identity-based application visibility. By managing bandwidth and traffic with unprecedented user and application visibility, the EX Series helps organizations of all sizes secure, optimize and scale their network edge and perimeter. By consolidating multiple WAN bandwidth management functions into one optimized management platform, organizations can greatly simplify their management of edge services, and increase performance and reliability for applications.
|
 |
 |
 |
| Key Features |
 |
Application Bandwidth Manager
Instant Application & User Visibility
Traffic Optimization
Security, Scalability & Reliability
|
 |
APPLICATION BANDWIDTH MANAGER
Maximum Bandwidth Control and Flexibility Through Comprehensive Feature Set with 2 Gigabits of Traffic-Shaping Performance |
 |
The EX Series can quickly eliminate bandwidth chokepoints to allow corporations to scale their applications, WAN and Internet traffic connections cost effectively and efficiently.
Comprehensive Protocol Support
Maximize bandwidth with support for over 100 business applications to ensure that the most critical network traffic receives the highest priority across WAN links. The EX provides automatic application protocol classification, comprehensive policies and traffic controls such as rate shaping, rate limiting, selective dropping and priority marking.
Application Protocol Classification
Application protocol classification techniques extend above simple Layer 3 and 4 (IP and port) combinations. Using A10’s deep packet inspection techniques enables the EX to identify application protocols for positive application identification. These techniques enable the EX to identify application protocols that use port hopping, port tunneling, and encryption.
Innovative User-Based QoS Policies
Allocate bandwidth and network application access transparently to users based solely on their user IDs. Practically any corporate data store such as Active Directory, SQL database and LDAP is available when connecting to an A10 ID Series appliance. Traditional QoS policies based on Layer 3-7 traffic classification can also be used to control bandwidth consumption.
Bandwidth Utilization Reports
Bandwidth utilization reports quickly identify top protocols, and users consuming too much bandwidth. Graphical real-time and historical reports with drill-down capabilities are available from the Web user interface. PDF or XML formatted reports may be exported manually or emailed periodically on a configurable schedule.
INSTANT APPLICATION & USER VISIBILITY
Industry's First Bandwidth Manager with Instant Application and User Visibility
See Who is Doing What and When Instantly
Accurately identifying the types of applications that are traversing the WAN and the amount of bandwidth they're consuming is one of the toughest challenges network administrators face. The EX Series solves this challenge with the ability to automatically detect popular business applications traversing the WAN—such as P2P, IM and email. With detailed reports outlining bandwidth usage patterns, top talkers, granular traffic-shaping and traffic distribution capabilities, administrators can quickly identify, limit and control applications to prioritize traffic flows.
High Level Data Leakage Monitoring
Application visibility allows a comprehensive log of application data and a free-form text search engine to pinpoint data of interest. In the case of a file transfer, the search flexibility allows viewing of application data to see the original location, filename, user actions to the file and source IP address (or user ID). EX strikes the balance between useful information and administration overhead.
The EX Series can also automatically track the use of popular file transfers, email, and instant messaging applications back to the originating user—helping IT engineers instantly see "who is using which applications." When combined with IDsentrie's IP-to-ID technology, the EX Series can instantly track the use of any WAN application back to the originating user to provide rich identity-based reports and help troubleshoot network and security problems quickly.
TRAFFIC OPTIMIZATION
Ensure Link-Level Redundancy and Optimize Network Traffic Over the WAN
To help organizations scale and increase delivery time for traffic over the WAN, the EX Series offers several advanced features.
Link Load Balancing
Supporting multi-homed networks with fine-grained load balancing across two or more WAN links to help increase WAN capacity, ensure link-level redundancy and optimize network traffic over the WAN. EX uniquely enables load balancing by application protocol. This allows mission-critical applications to use highly available dedicated links and non-critical applications such as Web surfing or multimedia to use links with lower service level agreements.
SECURITY, SCALABILITY & RELIABILITY
Enhanced Security, Scalability and Reliability for Non-Stop Performance
To help organizations scale and increase delivery time for traffic over the WAN, the EX Series offers several advanced features.
To provide high-performance and continuous service, A10 engineers architected a scalable multi-threaded operating system to fully take advantage of the latest multi-CPU technologies. With redundant hot swappable hard drives, advanced power supplies, and smart fans, the EX Series provides robust chassis-based failover protection. To protect against chassis failure, the EX Series supports HA pairing—ensuring uninterruptible service for critical WAN and perimeter applications. These capabilities are built upon a secure platform to optimize the network edge.
Network IPS
Identifying network anomalies before they impact your internal machines. Providing real time protection against attacks such as Distributed Denial of Service (DDoS), port scans, address sweeps, protocol misuse and malformed packets.
Performance
Delivering up to 2Gbps (EX 2000) and up to 500Mbps (EX 1000) of aggregate throughput and rate shaping/limiting capabilities, based on an optimized, purpose-built, high-performance processing architecture.
Flexible Deployment Options
It integrates into existing network infrastructures with support for both transparent and gateway modes, allowing fail open or closed configurations. Transparent mode also means no network configuration is changed for seamless deployment.
The EX Series provides 2 Gigabits/second of managed services to secure, optimize, and accelerate the network edge. With a high port density of 8, 10 or 12 Gigabit ports running in either Route Mode or Transparent Mode, customers can quickly aggregate and combine multiple network segments and zones that used to be managed separately at the network’s edge.
Internet connections, ecommerce applications, corporate email, public Web site zones, WAN links, and more can now be managed from one central secure high-performance platform with instant WAN application and user visibility.
|
|
 |



























